My journey to OSCP
Adam Hassan / February 2024 (2222 Words, 13 Minutes)
Table of contents
- Table of contents
- Getting started
- My background
- Actually studying
- The exam
- My tips to you
- What’s next?
Getting started
I started my OSCP in September of 2023 after purchasing the 3 month course with one exam attempt. Truthfully, as someone who doesn’t like to spend money, this was a hard thing to do, especially since OffSec does little in the way of helping out students with costs (see my mini-rant on the oscp subreddit here)
My background
I technically started doing HackTheBox and the like just about 5-6 years ago when I was in high school. I say ‘technically’, though, because I truly was clueless at the time and for at least 4 years since my “start”, I remember being unable to do anything technical other than run msfconsole, set rhosts, and hope for the best.
I’d say I actually started studying when I joined my university’s cybersecurity club, UFSIT. Here, I had actual resources and was able to ask for help. The competitions I was in helped immensely with gaining the motivation to actually practice. One thing it especially helped with was Windows and AD. In the summer before deciding to purchase the course, I spent practically every day learning about Windows and AD security concepts from TCM Security videos and by watching livestreams from BHIS and Antisyphon Training. I was lucky enough to have interned with a great company, Silicon Labs, where my mentor let me spend some of my time there on my own personal learning, which helped a lot considering the amount of extra time I was able to put into studying.
The TCM Security videos were great for learning AD concepts and I’d argue the content - especially the videos - is much higher quality than the OSCP course material.
One note here:
I purchased the subscription for a few months, but I ultimately don't think paying was worth it. TCM Security is kind enough to publish only slightly old versions of their content online for free. You can see the pentesting course here.
Actually studying
After I bought the course, those three months came and went before I could do much of anything. I remember scheduling my exam for a week after my course access expired, but because of my procrastination, schoolwork, and competition prep, I let the course access expire without doing much on it.
I don’t remember my course progress, but my guess is I skimmed through about 50% of the material and did about 10%-20% of the labs. Much to my detriment, I also was unable to do any of the challenge labs (Medtech, Relia…), which I really regretted, since it probably would have been the best indicator of readiness before the exam.
Letting the course expire felt like a huge waste, but I rationalized to myself that it was okay since I needed to buy the course to take the exam.
Because I let the course expire without studying much, I ended up delaying my exam the maximum amount of times and eventually took the exam just 2 months after I was originally scheduled to take it. At first, I just skimmed the pen-200 pdf, but this is what I did in the month before the exam:
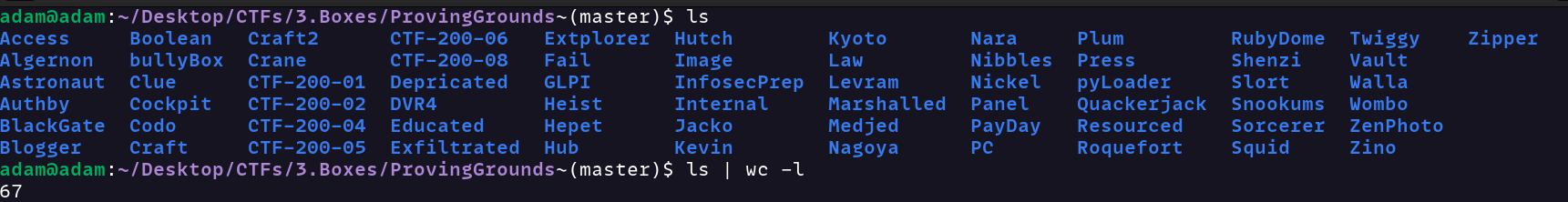
- I did every TJNull ProvingGrounds machine and then some extras. In total, I ended with 67 machines fully rooted.
- Note that I did use hints for quite a few of these, but I tried my hardest to not do so in the week before my exam.
- During that week, I did 18 machines (mostly intermediate and some easy community-rated ones) and was able to solve almost all of them in under an hour without any hints.
- Since PG Practice doesn’t have many easy Windows machines, I also bought access to VulnLab and followed their Active Directory Pentesting path.
- These took me a bit longer than the PG machines, but it was great to have extra AD machines (VulnLab has some chains / networks) to practice before the exam. I did 8 of these in total, but did need hints for the last few.
Overall, I’d say my last week of studying didn’t really teach me anything new (with the exception being the intermediate VulnLab machines), but they did help me with keeping things fresh before the exam.
While I was doing the PG machines, I didn’t actually write up anything (although I think I definitely should have at least taken brief notes about my workflow, challenges, etc.). However, I did slowly add to a very very rough AD and Linux cheat sheet, which I’ve posted here.
The exam
I had my exam scheduled for February 17th at 11 AM. I woke up that day around 7 AM and prepared to log on to proctoring which, despite my desire to join early, only let me in 15 minutes beforehand. I was worried the night before that my Debian 12 machine running Wayland wouldn’t work, as it isn’t officially supported, but everything worked perfectly.
Wave 1
I jumped between the boxes in my exam quite often, so I’ve decided to describe in terms of “waves” to organize things chronologically.
I started with the AD set
The AD set
The first machine, MS01, took me only about half an hour to get initial access to, and then about another 10 minutes to privesc on. I thought this was a great start and was fully expecting to fly through the AD set after all of my practice.
Unfortunately, after two more hours of trying to pivot from MS01 to MS02, I was completely unable. I had an idea of what I had to do, but I couldn’t execute.
To make sure I didn’t spend all my time on one thing (and partially to stop myself from going mad), I moved on to the standalone machines:
Standalone A
I heard from a lot of people that the OSCP has a lot of rabbit holes - something I was scared of, as all of the PG practice machines were very straightforward. It’s possible that I just got lucky with my exam set, but I found the machines to also be very straightforward. If I recall correctly, this machine only had 3 services, and it was quite obvious where the vuln was. I got initial access here in 15 minutes and then privesc in 5.
Standalone B
This machine also had only 2 or 3 services, but I still couldn’t figure out how to get initial access. I knew what I had to exploit, but only had a vague idea of how. After about half an hour here, I moved on to the third standalone.
Standalone C
For this machine, there were several services. I searched for probably an hour or so but was unable to make any tangible progress. I found a couple of minor vulnerabilities but had no idea if they were exploitable. I ended up not doing this machine and instead reporting the vulns as “informational” on my report.
Wave 2
After struggling with the second and third standalone, I decided to take a short 5 or 10 minute break before starting again.
Somehow, in that short break, I came up with an idea to get initial access for the 2nd standalone and got the local.txt flag. At this point, I had what I needed for the standalones, so I didn’t bother to privesc just yet.
I was feeling pretty good at this point. It was around 5 PM (6 hours in), and I had 30 points from the standalones. I told myself that all I needed was to finish AD and I would pass.
One note here:
I had pre-prepared food for my exam, which honestly was really helpful. I didn't have to spend time cooking, and I had a good meal to give me energy for the rest of the exam. I'd recommend doing the same thing if you can.
Because I knew I had to get DA to pass the exam, I went back to the AD set.
I worked on this for about 5 hours. I tried complicated exploits that I barely understood and none of them seemed to work.
Eventually, I was feeling pretty hopeless. It was around 9 PM (10 hours after I had started) and I only really had 20 points. I decided to take my first real break to clear my mind.
Before coming back, I had decided that I was going to write up a partial report with everything I’d found so far, and then continue with pentesting.
Filling in my report took about an hour, and then I started again with AD:
The AD set (again)
This time, I decided to redo all of the steps in my cheat sheet slowly.
I won’t re-write everything from my cheat sheet, but it was something along the lines of:
nmapscan- check smb anonymous and null auth with
nxc - run
enum4linux-ng ldapsearchcheck for cves- …
Now, out of caution, I won’t explain anything in detail, but there are some steps I skipped because I thought to myself:
There’s no way this would be on the OSCP, right?
I was, in fact, not right.
After doing a full enumeration and not skipping any steps, I found a vulnerability.
After 20 minutes of enumeration, I had gotten access to MS02 and then privesced to DC01 in another 5. I was ecstatic.
Wait, I thought the OSCP required you to pivot from MS01 to MS02?
network 1 network 2
kali <---------------> MS01 <--------------> MS02
<--------------> DC01
Yeah, I thought so too. I honestly thought I found an unintentional vuln on the domain, but my proctor assured me that any attack leading to getting the flags was valid.
I took the appropriate screenshots and then filled in my report.
Standalone B (again)
At this point, I had 70 points, but I decided to go for a privesc on this standalone. I tried running winPEAS and Seatbelt, but after some manual enumeration, I found a likely privesc and had admin 20 minutes later.
The report
At this point, I had already done most of the report, so instead of trying to finish the last standalone, I just refined my report. I filled in the introduction, recommendations, and the other things listed in the default OSCP template. I eventually submitted at 2 AM (15 hours after I started) and ended my exam.
One note here:
I'd recommend not doing what I did and actually taking the second day to look over your report (after getting a good night of sleep). While my report was fine, I definitely could have taken the time to improve on it and fix some minor typos.
The result
I passed!

My tips to you
- KISS: Keep it simple, stupid.
- Trying overly complicated exploits did not work for me at all. I may have just gotten lucky but in the 5 machines that I did get, I didn’t do a single custom exploit. Everything was either a simple misconfiguration or a CVE.
- I personally also didn’t get anything useful from automated tools. I only tried automated tools once (
winPEASandSeatbelt) and it got me nothing. Manual recon is the way.- I love having a simple methodology. I’ve taken a lot of inspiration from ippsec here. Know your tools, know your basic concepts - and your attack paths will be quick and simple.
- RAYG: Report as you go.
- Taking screenshots of everything you run and taking notes of what you’ve tried will make reporting in the end much easier.
- If possible, do everything in a tmux session that logs your commands/outputs to a file. This is good practice for real pentests.
- Take breaks:
- No, I don’t mean 5 minute breaks to go to the bathroom. I mean real breaks. I did this once before my little AD breakthrough and also right before finishing up my report. I probably should have done it more. The exam is 24 hours for a reason, and I think taking a break will make it much easier to collect your thoughts and do well
- Sleep and eat:
- I mentioned this earlier, but having good food made before the exam was very nice to have. Working with enough sleep also really ensured that I had the mental strength to not give up after 5 hours of failing.
What’s next?
Something I’ve been thinking about since before I signed up for the OSCP was that I wanted to do the CRTO and CRTL.
I’ve become very interested in evasion techniques and red teaming recently, and those certs could definitely help with improving on my skills there.
For now though, I’m going to take a bit of a break and work on some other things.
Currently, I’m doing an individual study at school that involves researching/implementing AV/EDR evasion techniques (something I’ll definitely have to write a lengthy blogpost about soon).
I’m also trying to get better at AD by doing more VulnLab. Indeed, while I thought I was pretty good at AD before the OSCP exam, my failed 5 hour attempt at complicated ways of moving laterally has led me to believe that I will truly never understand Kerberos.
Thanks for reading!
If you have any questions, feel free to reach out to me on discord or twitter (@adamkadaban)